Australia's Treasury Department has released a Sustainable Finance Roadmap to empower companies and...

At Auquan, we need a way to simplify the management of authentication keys, which our compute instances across multiple cloud platforms use to access documents stored in AWS S3. To accomplish this we implemented the Unified Key Orchestrator (UKO) from IBM Hyper Protect Crypto Services (HPCS).
We built Auquan’s Portfolio Intelligence Engine using a multi-cloud architecture with many of our applications running in vanilla compute instances within the premises of these cloud services. The applications running in these instances need to access certain documents stored in AWS S3 in a secure way.
Our objective is to manage the life cycle and usage of the access keys in a highly secure way, and we’re approaching this implementation in two phases.
IBM HPCS UKO can manage keys securely across multiple z/OS systems and across other cloud providers, including Microsoft Azure, Amazon Web Services (AWS), IBM Cloud, and Google Cloud Platform.
All of the keys in all those places are protected by a master key, which is stored in a FIPS 140-2 Level 4-certified hardware security module (HSM) for the highest security. One can manage the life cycles of the keys from a single point of control, while the system keeps keys that are distributed in sync.
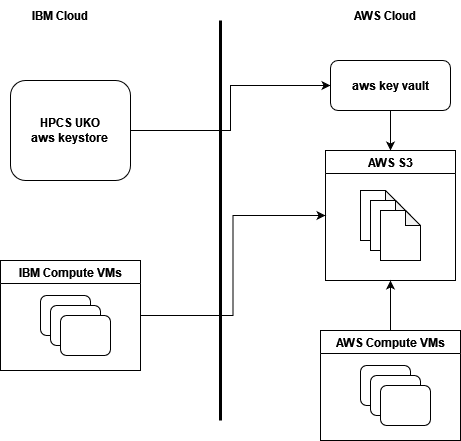
In our use case, our compute instances in IBM cloud and those running in AWS are both accessing documents stored in AWS S3, secured and encrypted by a key in AWS key vault. However, this key is being managed by the keystore in HPCS UKO, which provides a seamless experience across cloud providers to manage the security life-cycle of the documents.
Each day we spotlight under-the-radar investment themes and idiosyncratic risks pulled from our intelligence engine, often involving emerging markets, supply chain issues, ESG risks, and the impact of regulatory changes.

Australia's Treasury Department has released a Sustainable Finance Roadmap to empower companies and...
.png?height=200&name=News%20Cover%20(87).png)
The International Sustainability Standards Board (ISSB) has released an Exposure Draft proposing a...
.png?height=200&name=News%20Cover%20(86).png)
The Canadian Securities Administrators (CSA), Canada's security regulator, have announced that they...
Each day we spotlight under-the-radar investment themes and idiosyncratic risks pulled from our intelligence engine, often involving emerging markets, supply chain issues, ESG risks, and the impact of regulatory changes.

15 minutes to see what’s possible when manual work disappears.
Interested in working at Auquan? Click here
At Auquan, we need a way to simplify the management of authentication keys, which our compute instances across multiple cloud platforms use to access documents stored in AWS S3. To accomplish this we implemented the Unified Key Orchestrator (UKO) from IBM Hyper Protect Crypto Services (HPCS).
We built Auquan’s Portfolio Intelligence Engine using a multi-cloud architecture with many of our applications running in vanilla compute instances within the premises of these cloud services. The applications running in these instances need to access certain documents stored in AWS S3 in a secure way.
Our objective is to manage the life cycle and usage of the access keys in a highly secure way, and we’re approaching this implementation in two phases.
IBM HPCS UKO can manage keys securely across multiple z/OS systems and across other cloud providers, including Microsoft Azure, Amazon Web Services (AWS), IBM Cloud, and Google Cloud Platform.
All of the keys in all those places are protected by a master key, which is stored in a FIPS 140-2 Level 4-certified hardware security module (HSM) for the highest security. One can manage the life cycles of the keys from a single point of control, while the system keeps keys that are distributed in sync.

In our use case, our compute instances in IBM cloud and those running in AWS are both accessing documents stored in AWS S3, secured and encrypted by a key in AWS key vault. However, this key is being managed by the keystore in HPCS UKO, which provides a seamless experience across cloud providers to manage the security life-cycle of the documents.
Each day we spotlight under-the-radar investment themes and idiosyncratic risks pulled from our intelligence engine, often involving emerging markets, supply chain issues, ESG risks, and the impact of regulatory changes.

Australia's Treasury Department has released a Sustainable Finance Roadmap to empower companies and...
.png?height=200&name=News%20Cover%20(87).png)
The International Sustainability Standards Board (ISSB) has released an Exposure Draft proposing a...
.png?height=200&name=News%20Cover%20(86).png)
The Canadian Securities Administrators (CSA), Canada's security regulator, have announced that they...
15 minutes to see what’s possible when manual work disappears.
Interested in working at Auquan? Click here
